Route 53
Create verification records in Route 53 DNS
| Plugin type | DNS validation | |
|---|---|---|
| Download | Version v2.3.5. Look for older releases on GitHub for files named like plugin.validation.dns.route53.v2.x.x.zip | |
| Chocolatey | choco install simple-acme-validation-dns-route53(details) |
|
| Compatibility | All platforms |
Description
Create the record in Amazon AWS Route53. This requires either a user or an IAM role with the following permissions on the zone:
route53:GetChange, route53:ListHostedZones and route53:ChangeResourceRecordSets.
IAM
The IAM role method can only work from inside an EC2 instance. Note that the program expects to recieve an IAM role name, so not the full ARN.
ARN
The ARN role method can work from anywhere.
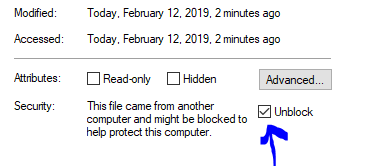
Plugins needs to be unpacked into a folder called %programdata%\simple-acme\plugins. Depending on how you downloaded the file, you may have to unblock the .dll files before your computer will trust them. You can do that from the File Explorer by using the right mouse button and then checking the `Unblock` box on the General tab.
To verify that the plugin is properly installed you can start the main executable
with ‑‑verbose and it will print information about found and loaded plugins at
start up. When the plugin is loaded, it manifests itself as extra menu choices and
command line parameters being made availalbe.
All releases published to third party package managers like Chocolatey and NuGet support plugins, but if you download simple-acme manually, you must choose a pluggable version instead of the trimmed one to use it.
Command line
--validation route53 |
Activates the plugin | |
|---|---|---|
‑‑route53region |
AWS region to use for authentication (default: us-east-1) | |
‑‑route53iamrole |
AWS IAM role for the current EC2 instance to login. Note that you should provide the IAM name instead of the ARN. | |
‑‑route53arnrole |
AWS role ARN for the current EC2 instance to login. This may be a full ARN. | |
‑‑route53accesskeyid |
Access key ID to login into Amazon Route 53. | |
‑‑route53secretaccesskey |
Secret access key to login into Amazon Route 53.
You may pass the secret in plain text, but can also use a reference to the secret vault like |
Examples
| Access key | --validation route53 ‑‑route53accesskeyid mykeyid ‑‑route53secretaccesskey ***** |
|
|---|---|---|
| IAM role | --validation route53 ‑‑route53iamrole myrole |
|
| ARN role (using instance profile) | --validation route53 ‑‑route53arnrole "arn:aws:iam::123456789012:user/johndoe" |
|
| ARN role (using IAM role) | --validation route53 ‑‑route53iamrole myrole ‑‑route53arnrole "arn:aws:iam::123456789012:user/johndoe" |
|
| ARN role (using access key) | --validation route53 ‑‑route53accesskeyid mykeyid ‑‑route53secretaccesskey ***** ‑‑route53arnrole "arn:aws:iam::123456789012:user/johndoe" |
JSON
| ID | 4e5dc595-45c7-4461-929a-8f96a0c96b3d |
|---|
Looking for win-acme?
simple-acme is a backwards compatible, drop-in replacement built by the same person. Project history.
